Secure & Manage Devices using the Microsoft Intune Suite with AVASOFT
AVASOFT
Seamlessly secure devices with Microsoft Intune. Simplify management, protect against cyber threats, and ensure robust endpoint protection. Tailored solutions for peace of mind
Seamlessly secure devices with Microsoft Intune. Simplify management, protect against cyber threats, and ensure robust endpoint protection. Tailored solutions for peace of mind
Device Security Management with Microsoft Intune
Goal:
Our consulting services aim to help you get started with or extend your use of Microsoft 365 by providing the necessary expertise, capabilities, and know-how that you may lack in-house or need to enhance.
Approach:
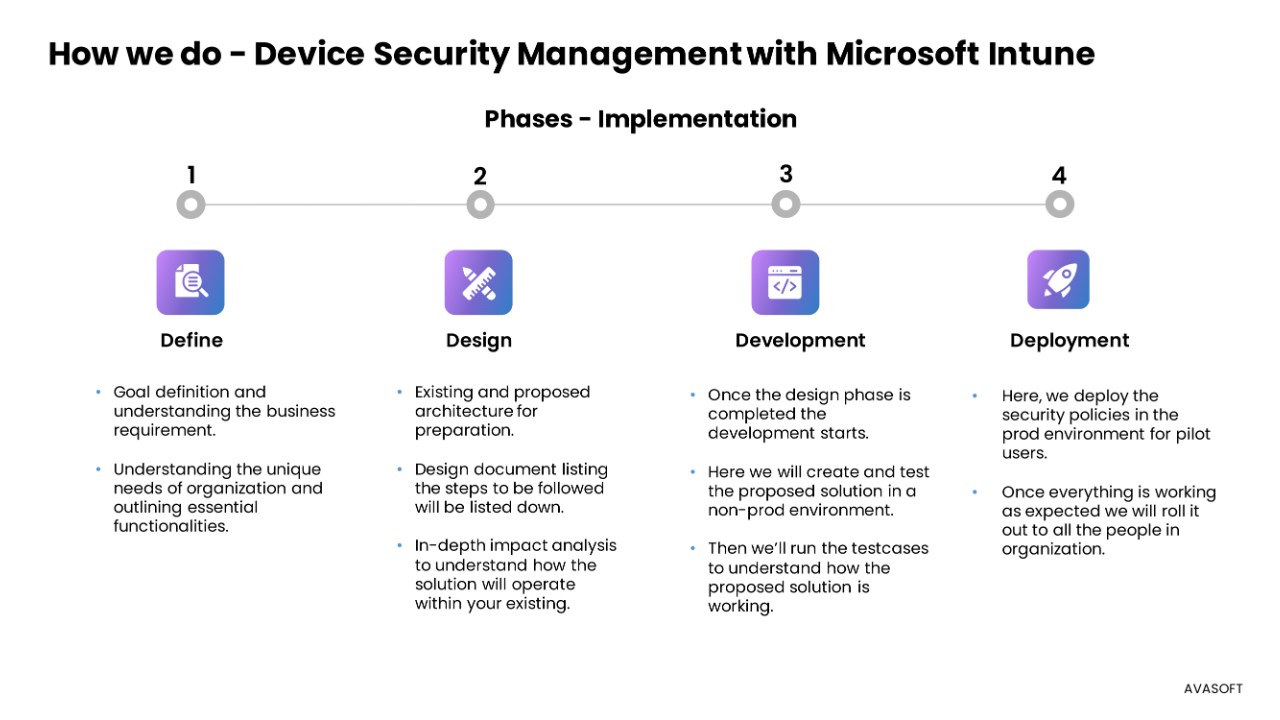
Our approach unfolds in the following stages:
- Define
- Design
- Develop
- Deploy
1. Define
- Goal Definition: Understand your business requirements.
- Requirement Analysis: Understand the unique needs of your organization and outline essential functionalities.
2. Design
- Architecture Preparation: Document existing and proposed architectures.
- Design Documentation: List the steps to be followed.
- Impact Analysis: Conduct an in-depth impact analysis to understand how the solution will operate within your existing infrastructure.
3. Develop
- Development: Create and test the proposed solution in a non-prod environment.
- Testing: Run test cases to ensure the proposed solution works as expected.
4. Deploy
- Pilot Deployment: Deploy security policies in the prod environment for pilot users.
- Full Rollout: Once everything is working as expected, roll out the solution to the entire organization.
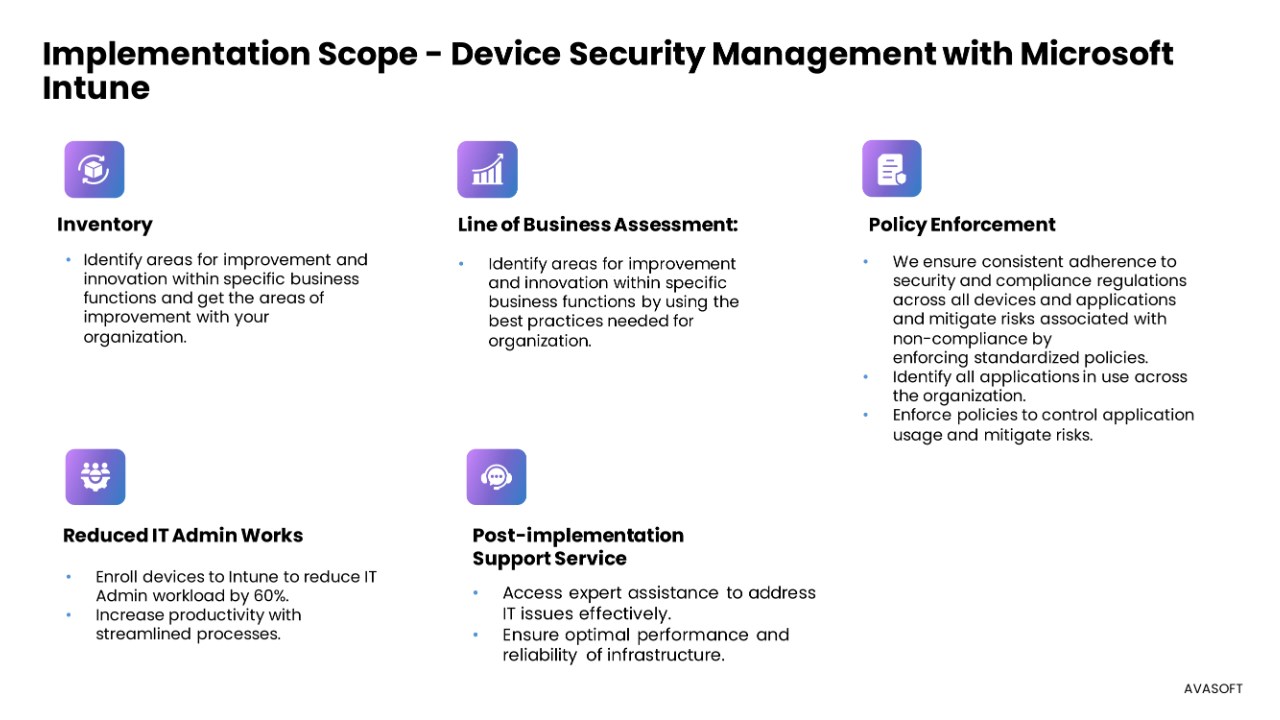
What We Do:
- Inventory
- Line of Business Assessment
- Policy Enforcement
- Reduced IT Admin Work
- Application Discovery and Enforcement
- Managed Support Service
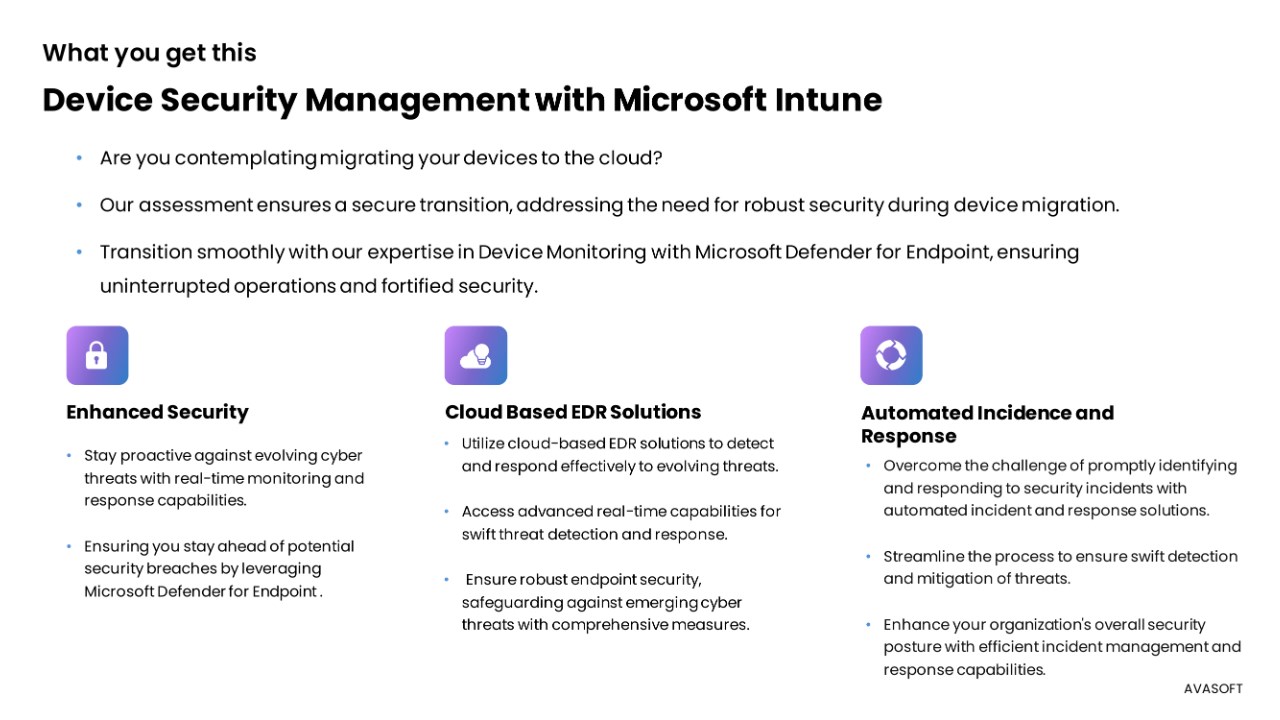
Key Benefits:
- Elevated Device Security: Use Microsoft Intune's MDM and MAM features to secure numerous devices, providing centralized control, secure app distribution, and easy management for security and compliance.
- Streamlined Device Management: Utilize Unified Endpoint Management (UEM) for a centralized approach to managing all devices from a single console.
- Comprehensive Analytics: Gain deep insights into device performance, security threats, and user behavior, enabling informed decision-making and proactive risk mitigation.
Deliverables:
- Centralized Device Management: Manage all devices from one place, cutting costs and gaining better oversight of your infrastructure.
- Optimized Operations: Deploy streamlined processes for better visibility and control over device management, optimizing operations in the cloud.
- Scalability and Flexibility: Experience effortless scalability and flexibility with centralized device management, simplifying troubleshooting and ensuring adaptability.
By leveraging AVASOFT's structured approach, your organization can efficiently manage device security using Microsoft Intune, ensuring a secure and compliant environment while optimizing operational costs.
For more information, please contact us to learn how AVASOFT can help you with device security management using Microsoft Intune.
De un vistazo